
26 May 2023
Precision Targeted Training For Developers
Find out how you can use Dracon to suggest laser-focused training to each developer based on tooling findings, with no code
Precision Targeted Training For Developers
This is the second blogpost in a series of how we leverage modern NLP technology to enrich tooling data for many different use cases.
Introduction
Security training is a bit like cooking, following advice or copying existing recipes is doable and sometimes even, good enough.
However, it requires deep mastery of the field and attention to the finer details in order to produce a result that is both appealing to the audience and good for them.
Same as a good cook, a good security trainer needs to target the audience’s specific needs and on top of that needs to be able explain their message in a way that is relevant to the audience’s prior experience and existing problems. But even in this case each not each training exercise or lab is suitable to every development team. For example, if a team develops only a backend service, they probably do not care about Cross Site Scripting or other client-side attacks.
Both in our market research and our talks with customers we have found out that often, matching training to developers or development teams is a manual process, which does not scale and is not very interesting.
So we automated it.
Using Ocurity, Dracon-SaaS customers can aggregate all results from any security scanning solution.
Since Dracon-SaaS has access to the results, then it would be relatively simple to use our Correlation Engine to provide suggestions for the most relevant training picked from the list available from the training provider any customer wants.
Since screenshots speak louder than words, let’s demonstrate this.
Use case
In this blogpost we showcase how we use a Training Enricher to automatically find the security areas each Developer is weakest at and suggest relevant training.
The Training enricher works by downloading metadata from several training providers or vulnerable applications both free e.g. OWASP Juice Shop, Secure Knowledge Framework and proprietary.
Then it uses our correlation engine to associate tooling findings with the most relevant training from each provider.
The result is that each finding gets enriched with one or more links to training a developer could take to get information on how to remediate the found issue.
To demonstrate this we will create a pipeline:
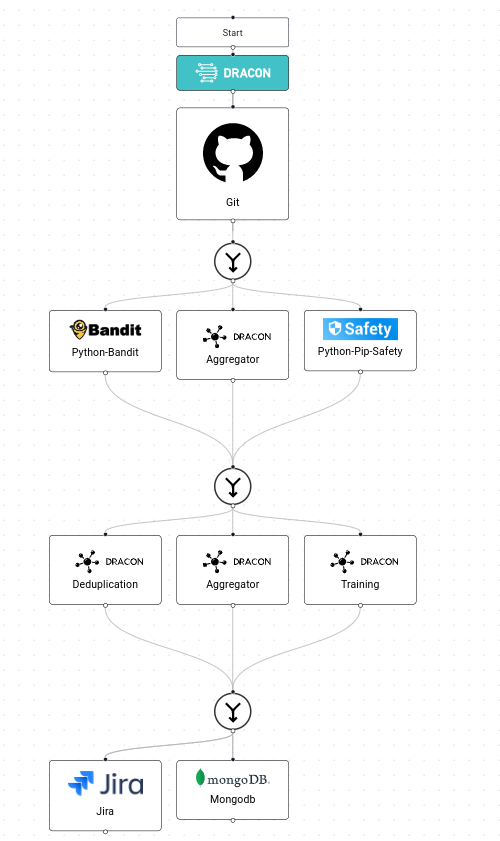
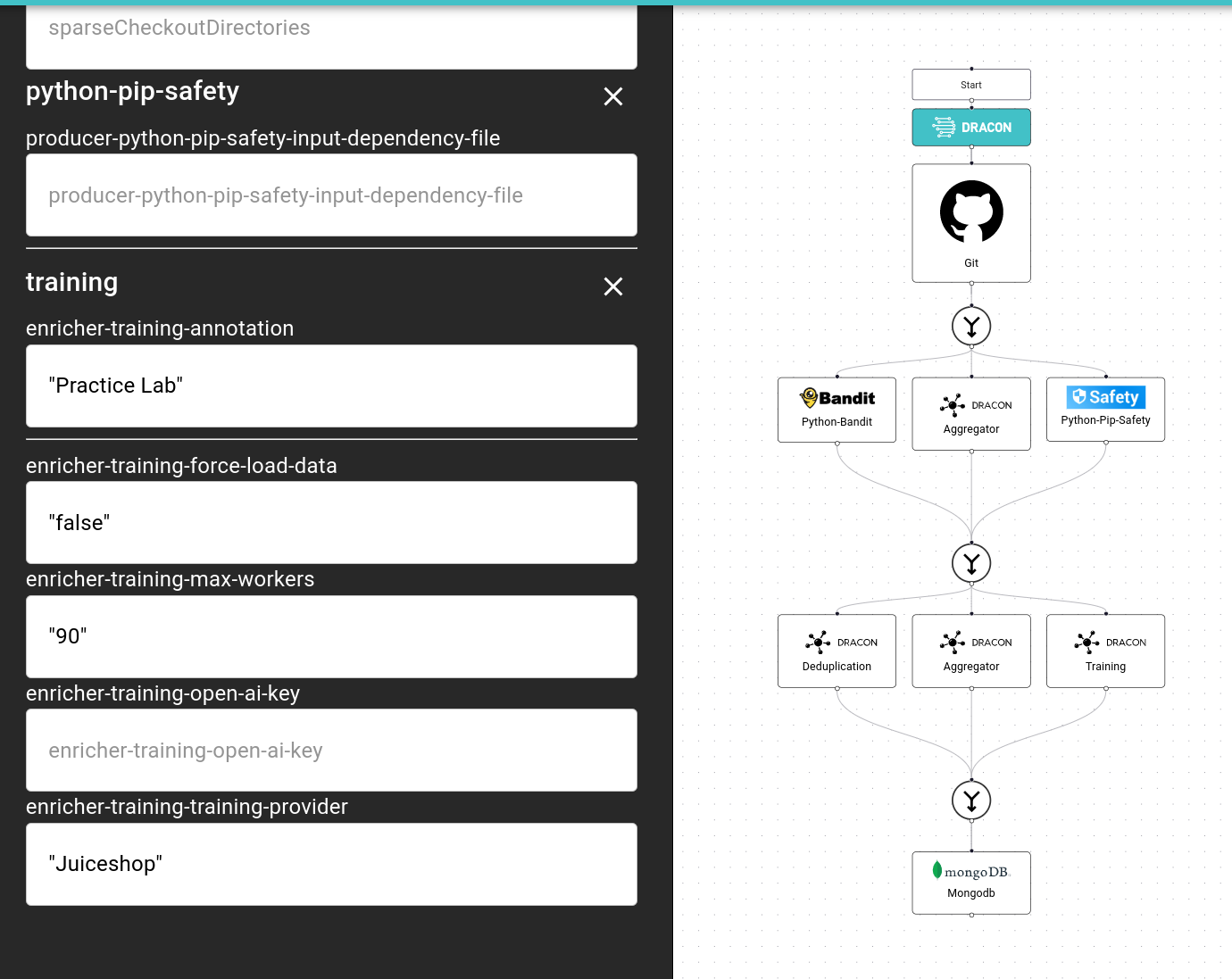
Then we just define the Training provider, in our case we can use OWASP Juiceshop for demonstration purposes. Juiceshop is a versatile and feature complete example vulnerable application maintained by Bjoern Kimminich under OWASP.
Executing this pipeline, gives us the following information:
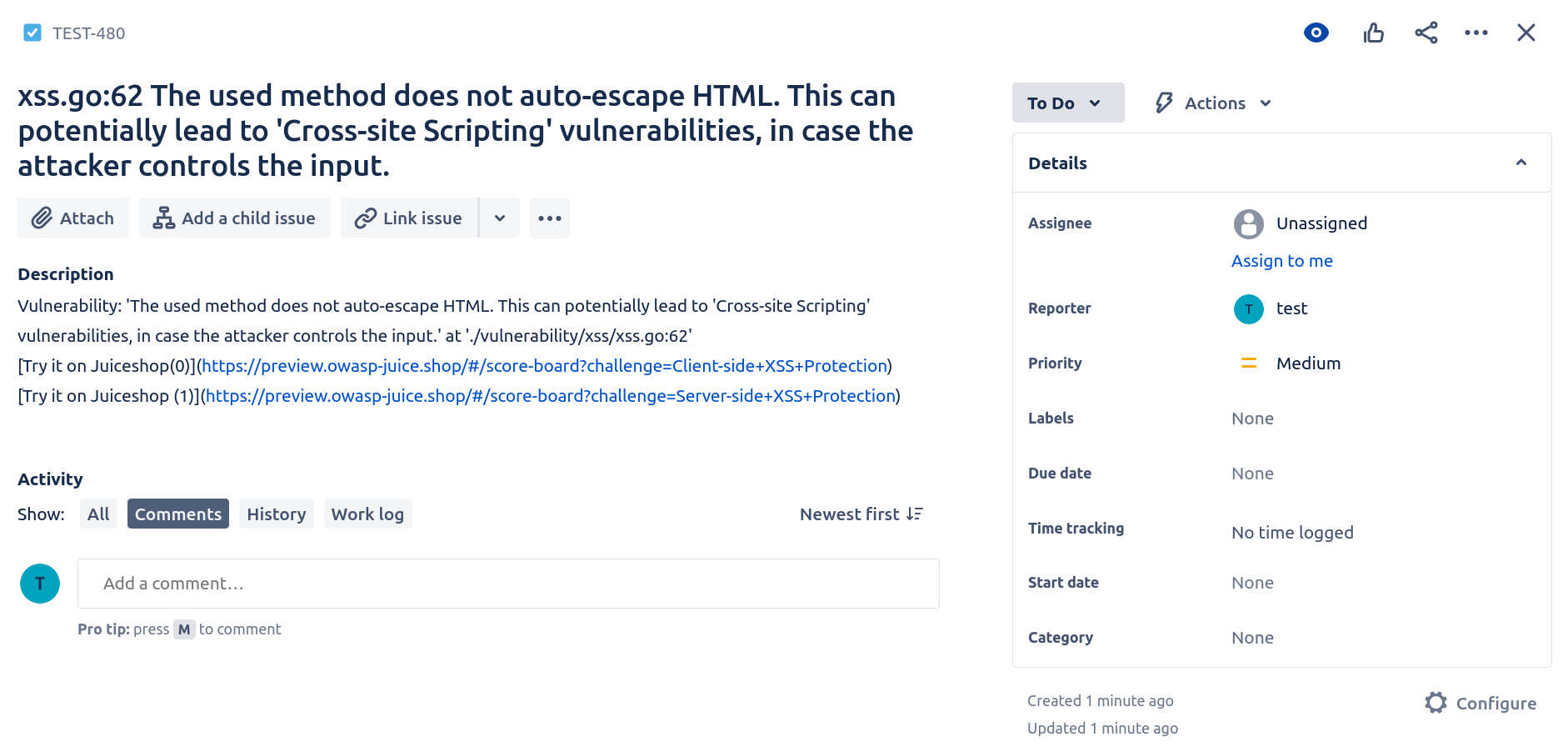
Using this functionality, development teams can now receive automated suggestions for training based on the most relevant information related to a finding. No more generic “please do at least 3 modules per quarter”.
If you are interested in Dracon, our revolutionary solution, let’s schedule a demo here.